概要
些文章将配置雅马哈路由器连接至Amazon Virtual Private Cloud(Amazon VPC)的设置例。
Amazon VPC可以实现将企业的内网连接至Amazon Web Services(AWS)的功能。
详细信息已在Web上公开,具体请参阅:技术资料(英语)
测试环境如下所示。
- 机型: RTX1200
- 固件版本号: Rev.10.01.29
- WAN线路: PPPoE连接(B Flet’s)
- 路由器LAN侧的IP地址: 192.168.0.1/24
※1: 这篇文章是基于2011年4月30日的规格。今后规格发生变更的话,根据变更的内容可能会发生按照本文的设置方法而不能连接的情况
Amazon VPC的设置
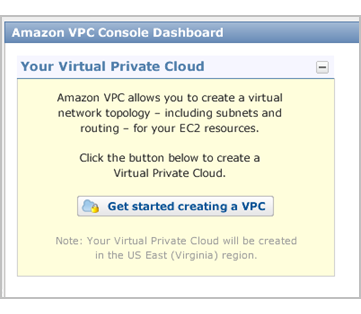
1. 向导开始
在「Amazon VPC Console Dashboard」中,单击「Get started creating a VPC」按钮。
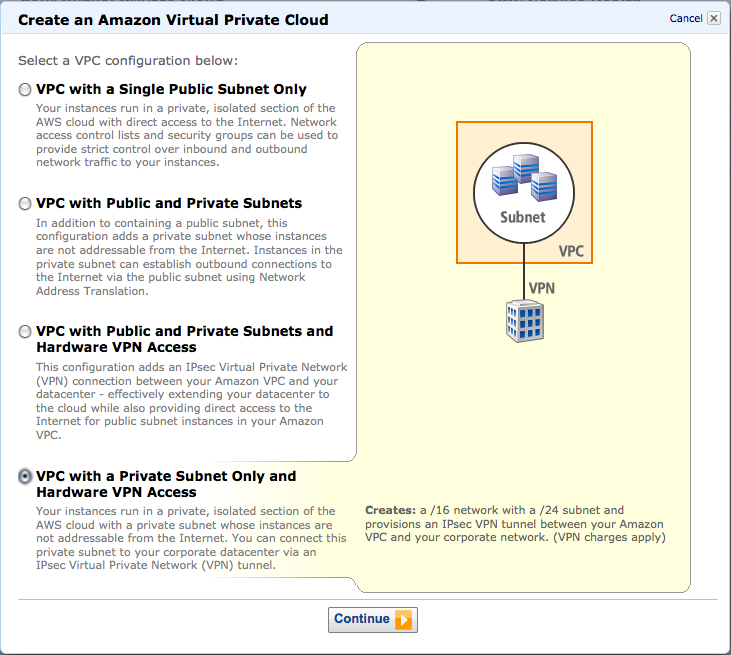
2. 选择网络结构
选择「VPC with a Private Subnet Only and Hardware VPN Access」、并单击「Continue」按钮。
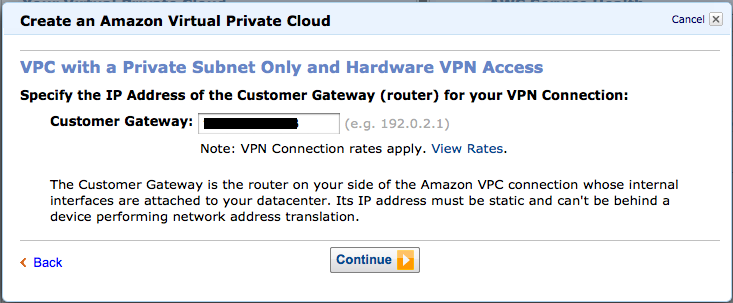
3. 设置路由器的IP地址
请在此输入符合实际情况的WAN侧的IP地址。输入完成后,按下「Continue」按钮。
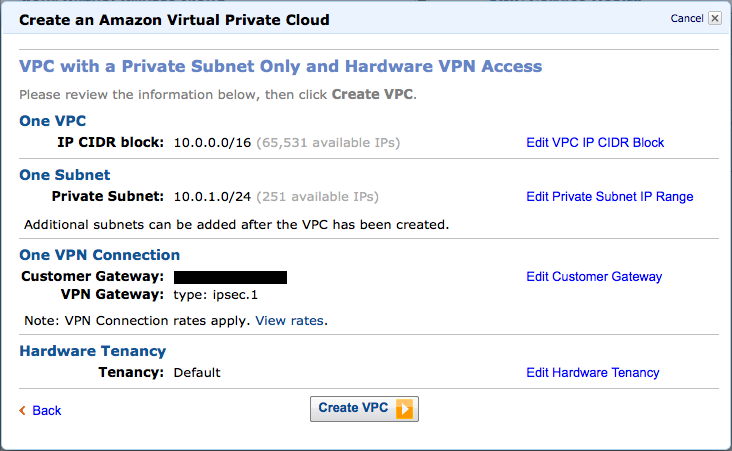
4. 设置的确认
如图显示的是VPN的设置。可以在此修改有问题的项目。
本次是按照默认的设置进行的、就按照如图所示的设置进行下一步。虽然可以登录多个子网、但在本次测试中,我们只测试1个子网。
确认设置无误后,单击「Create VPC」按钮。
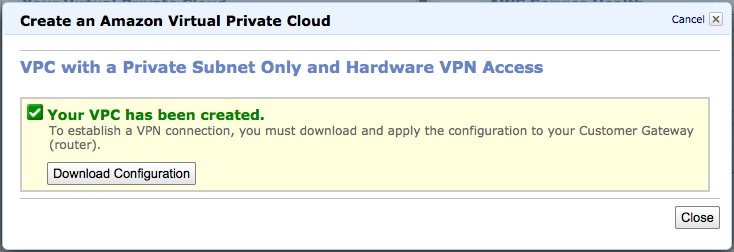
5. VPC生成
完成VPC的生成处理之后,将会显示如下的画面、请单击「Download Configuration」按钮。
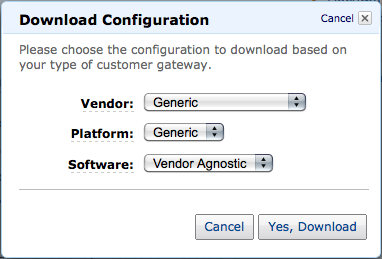
6. 下载设置
设置完成之后,可以下载对应路由器的设置例、请一定不要忘记下载。在Vendor和Platform中选择「Generic」、并单击「Yes, Download」按钮。
路由器的设置
将下载的设置例从头开始,边看边开始设置雅马哈路由器。
1. IPsec隧道(1)
首先,设置IKE。下载的设置例如下所示。
IPSec Tunnel #1
================================================
#1: Internet Key Exchange Configuration
Configure the IKE SA as follows
- Authentication Method : Pre-Shared Key
- Pre-Shared Key : PRE-SHARED-KEY1
- Authentication Algorithm : sha1
- Encryption Algorithm : aes-128-cbc
- Lifetime : 28800 seconds
- Phase 1 Negotiation Mode : main
- Perfect Forward Secrecy : Diffie-Hellman Group 2
相应的雅马哈路由器的设置如下所示。PRE-SHARED-KEY1的部分、实际上是随机的字符串、请按照如下的设置填入字符串。
# ipsec ike pre-shared-key 1 text PRE-SHARED-KEY1
# ipsec ike hash 1 sha
# ipsec ike encryption 1 aes-cbc
# ipsec ike duration isakmp-sa 1 28800
# ipsec ike group 1 modp1024
接下来是IPsec的设置。
#2: IPSec Configuration
Configure the IPSec SA as follows:
- Protocol : esp
- Authentication Algorithm : hmac-sha1-96
- Encryption Algorithm : aes-128-cbc
- Lifetime : 3600 seconds
- Mode : tunnel
- Perfect Forward Secrecy : Diffie-Hellman Group 2
相应的设置如下所示。
# ipsec sa policy 101 1 esp aes-cbc sha-hmac
# ipsec ike duration ipsec-sa 1 3600
# tunnel select 1
# ipsec tunnel 101
Dead Peer Detection(DPD)的设置。
IPSec Dead Peer Detection (DPD) will be enabled on the AWS Endpoint. We
recommend configuring DPD on your endpoint as follows:
- DPD Interval : 10
- DPD Retries : 3
使用ipsec ike keepalive use命令进行设置。
# ipsec ike keepalive use 1 on dpd 10 3
接下来是ESP的设置。
IPSec ESP (Encapsulating Security Payload) inserts additional
headers to transmit packets. These headers require additional space,
which reduces the amount of space available to transmit application data.
To limit the impact of this behavior, we recommend the following
configuration on your Customer Gateway:
- TCP MSS Adjustment : 1396 bytes
- Clear Don't Fragment Bit : enabled
- Fragmentation : Before encryption
相应的设置如下所示。
# tunnel select 1
# ip tunnel tcp mss limit 1396
# ipsec tunnel outer df-bit clear
# tunnel enable 1
这是IP地址的设置。实际的IP地址可能会与本示例不同、请根据实际情况设置。
Outside IP Addresses:
- Customer Gateway: : YOUR_UPLINK_ADDRESS
- VPN Gateway : 72.21.209.225
Inside IP Addresses
- Customer Gateway : 169.254.255.2/30
- VPN Gateway : 169.254.255.1/30
相应的设置如下所示。并不需要特别设置YOUR_UPLINK_ADDRESS。
在ipsec ike local address命令中、设置路由器LAN侧的IP地址。在本例中、使用192.168.0.1/24。
# ipsec ike local address 1 192.168.0.1
# ipsec ike remote address 1 72.21.209.225
# tunnel select 1
# ip tunnel address 169.254.255.2/30
# ip tunnel remote address 169.254.255.1
# tunnel enable 1
最后,进行BGP的设置。
#4: Border Gateway Protocol (BGP) Configuration:
The Border Gateway Protocol (BGPv4) is used within the tunnel, between the inside
IP addresses, to exchange routes from the VPC to your home network. Each
BGP router has an Autonomous System Number (ASN). Your ASN was provided
to AWS when the Customer Gateway was created.
BGP Configuration Options:
- Customer Gateway ASN : YOUR_BGP_ASN
- VPN Gateway ASN : 7224
- Neighbor IP Address : 169.254.255.1
- Neighbor Hold Time : 30
Configure BGP to announce the default route (0.0.0.0/0) to the VPN Connection
Gateway. The VPN Gateway will announce prefixes to your Customer
Gateway based upon the prefixes assigned in the creation of the VPC.
YOUR_BGP_ASN,实际上是65000这样的数字。和其他的项目一样,可能和本例中的数字不同、请根据实际情况进行设置。相应的设置如下所示。
# bgp autonomous-system YOUR_BGP_ASN
# bgp neighbor 1 7224 169.254.255.1 hold-time=30 local-address=169.254.255.2
# bgp import filter 1 equal 0.0.0.0/0
# bgp import 7224 static filter 1
2. IPsec隧道(2)
接下来进行第2条隧道的设置。
IPSec Tunnel #2
=====================================================
#1: Internet Key Exchange Configuration
Configure the IKE SA as follows
- Authentication Method : Pre-Shared Key
- Pre-Shared Key : PRE-SHARED-KEY2
- Authentication Algorithm : sha1
- Encryption Algorithm : aes-128-cbc
- Lifetime : 28800 seconds
- Phase 1 Negotiation Mode : main
- Perfect Forward Secrecy : Diffie-Hellman Group
相应的雅马哈路由器的设置如下所示。PRE-SHARED-KEY2的部分、实际上是随机的字符串、请按照如下的设置填入字符串。
# ipsec ike pre-shared-key 2 text PRE-SHARED-KEY2
# ipsec ike hash 2 sha
# ipsec ike encryption 2 aes-cbc
# ipsec ike duration isakmp-sa 2 28800
# ipsec ike group 2 modp1024
接下来是IPsec的设置。
#2: IPSec Configuration
Configure the IPSec SA as follows:
- Protocol : esp
- Authentication Algorithm : hmac-sha1-96
- Encryption Algorithm : aes-128-cbc
- Lifetime : 3600 seconds
- Mode : tunnel
- Perfect Forward Secrecy : Diffie-Hellman Group 2
相应的设置如下所示。
# ipsec sa policy 102 2 esp aes-cbc sha-hmac
# ipsec ike duration ipsec-sa 2 3600
# tunnel select 2
# ipsec tunnel 102
Dead Peer Detection(DPD)的设置。
IPSec Dead Peer Detection (DPD) will be enabled on the AWS Endpoint. We
recommend configuring DPD on your endpoint as follows:
- DPD Interval : 10
- DPD Retries : 3
使用ipsec ike keepalive use命令进行设置。
# ipsec ike keepalive use 2 on dpd 10 3
接下来是ESP的设置。
IPSec ESP (Encapsulating Security Payload) inserts additional
headers to transmit packets. These headers require additional space,
which reduces the amount of space available to transmit application data.
To limit the impact of this behavior, we recommend the following
configuration on your Customer Gateway:
- TCP MSS Adjustment : 1396 bytes
- Clear Don't Fragment Bit : enabled
- Fragmentation : Before encryption
相应的设置如下所示。
# tunnel select 2
# ip tunnel tcp mss limit 1396
# ipsec tunnel outer df-bit clear
# tunnel enable 2
这是IP地址的设置。实际的IP地址可能会与本示例不同、请根据实际情况设置。
Outside IP Addresses:
- Customer Gateway: : YOUR_UPLINK_ADDRESS
- VPN Gateway : 72.21.209.193
Inside IP Addresses
- Customer Gateway : 169.254.255.6/30
- VPN Gateway : 169.254.255.5/30
相应的设置如下所示。
# ipsec ike local address 2 192.168.0.1
# ipsec ike remote address 2 72.21.209.193
# tunnel select 2
# ip tunnel address 169.254.255.6/30
# ip tunnel remote address 169.254.255.5
# tunnel enable 2
最后是BGP的设置。
#4: Border Gateway Protocol (BGP) Configuration:
The Border Gateway Protocol (BGPv4) is used within the tunnel, between the inside
IP addresses, to exchange routes from the VPC to your home network. Each
BGP router has an Autonomous System Number (ASN). Your ASN was provided
to AWS when the Customer Gateway was created.
BGP Configuration Options:
- Customer Gateway ASN : YOUR_BGP_ASN
- VPN Gateway ASN : 7224
- Neighbor IP Address : 169.254.255.5
- Neighbor Hold Time : 30
Configure BGP to announce the default route (0.0.0.0/0) to the VPN Connection
Gateway. The VPN Gateway will announce prefixes to your Customer
Gateway based upon the prefixes assigned in the creation of the VPC.
因为刚才已经设置了YOUR_BGP_ASN和默认路由、所以此处只需如下一条设置即可。AS号和实际的IP地址可能会与本示例不同、请根据实际情况设置。
# bgp neighbor 2 7224 169.254.255.5 hold-time=30 local-address=169.254.255.6
3. 整体设置
需要增加路由器的整体动作相关的设置。
# bgp use on
# bgp configure refresh
# ipsec auto refresh on
不要忘了将设置进行保存。
包含PPPoE连接设置在内的整体设置例,可以在此进行下载。
运行确认
1. 确认IPsec的运行状态
首先、确认IPsec的工作状态。请运行show ipsec sa命令。
# show ipsec sa
Total: isakmp:2 send:2 recv:2
sa sgw isakmp connection dir life[s] remote-id
--------------------------------------------------------------------
1 1 - isakmp - 28779 72.21.209.225
2 2 - isakmp - 28780 72.21.209.193
3 1 1 tun[001]esp send 3581 72.21.209.225
4 1 1 tun[001]esp recv 3581 72.21.209.225
5 2 2 tun[002]esp send 3582 72.21.209.193
6 2 2 tun[002]esp recv 3582 72.21.209.193
如果没有显示出SA的信息、请重新检查一下设置。特别是ipsec ike pre-shared-key的设置容易发生错误、请仔细确认诸如「0(零)」和「O(字母)」的不同。
2. 确认BGP的运行状态
请使用show status bgp neighbor命令来确认2条连接是否已经启动。正常运行的话,就会如下图中的下划线部分所示,显示「Established」。
# show status bgp neighbor
BGP neighbor is 169.254.255.1, remote AS 7224, local AS 65000, external link
BGP version 4, remote router ID 169.254.255.1
BGP state = Established, up for 00:01:04
Last read 00:00:06, hold time is 30, keepalive interval is 10 seconds
Received 8 messages, 0 notifications, 0 in queue
Sent 12 messages, 1 notifications, 0 in queue
Connection established 1; dropped 0
Last reset never
Local host: 169.254.255.2, Local port: 1027
Foreign host: 169.254.255.1, Foreign port: 179
BGP neighbor is 169.254.255.5, remote AS 7224, local AS 65000, external link
BGP version 4, remote router ID 169.254.255.5
BGP state = Established, up for 00:00:58
Last read 00:00:09, hold time is 30, keepalive interval is 10 seconds
Received 7 messages, 0 notifications, 0 in queue
Sent 11 messages, 1 notifications, 0 in queue
Connection established 1; dropped 0
Last reset never
Local host: 169.254.255.6, Local port: 1028
Foreign host: 169.254.255.5, Foreign port: 179
如果没有任何显示的话,请确认一下设置。变更BGP的设置之后、请一定要运行bgp configure refresh命令、千万不要忘记。
3. 确认路由表
使用show ip route命令进行路由的确认。通过BGP接收到的路由、如下划线所示那样,显示为「BGP」。
# show ip route
Destination Gateway Interface Kind Additional Info.
default - PP[01] static
10.0.0.0/16 169.254.255.1 TUNNEL[1] BGP path=7224
169.254.255.0/30 - TUNNEL[1] implicit
169.254.255.4/30 - TUNNEL[2] implicit
192.168.0.0/24 192.168.0.1 LAN1 implicit
4. 通讯的确认
确认能否和VPC上的Instance进行通讯。Instance的作成方法请参考Amazon VPC的技术资料。使用ping命令来确认和Instance的IP地址间的连接性。
※如果遇到ping不通的情况、可能是在Amazon VPC的「Security Group」的设置中、禁止了ICMP的通信、请确认一下。
# ping 10.0.1.149
received from 10.0.1.149: icmp_seq=0 ttl=61 time=207.543ms
received from 10.0.1.149: icmp_seq=1 ttl=61 time=207.557ms
received from 10.0.1.149: icmp_seq=2 ttl=61 time=207.564ms
received from 10.0.1.149: icmp_seq=3 ttl=61 time=211.124ms
received from 10.0.1.149: icmp_seq=4 ttl=61 time=207.465ms
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max = 207.465/208.250/211.124 ms
5. 确认冗余的运行状态
检查一下在Amazon VPC的网关宕机时,冗余功能是否能正常工作。因为等待网关宕机实际上是不可能的、所以可以通过强制过滤掉BGP数据包来模拟故障的发生。
# ip filter 1 reject 169.254.255.1 * tcp bgp *
# ip filter 2 pass * * * * *
# tunnel select 1
# ip tunnel secure filter in 1 2
等待一会儿之后,BGP的连接就会中断、路由会发生变化。使用show ip route命令可以确认路由的变化。如下划线部分所示、网关由10.0.0.0/16变成了169.254.255.5。
# show ip route
Destination Gateway Interface Kind Additional Info.
default - PP[01] static
10.0.0.0/16 169.254.255.5 TUNNEL[2] BGP path=7224
169.254.255.0/30 - TUNNEL[1] implicit
169.254.255.4/30 - TUNNEL[2] implicit
192.168.0.0/24 192.168.0.1 LAN1 implicit
在这种状态下,ping一下Instance地址,确认能否正常通信。
# ping 10.0.1.149
received from 10.0.1.149: icmp_seq=0 ttl=61 time=202.155ms
received from 10.0.1.149: icmp_seq=1 ttl=61 time=201.853ms
received from 10.0.1.149: icmp_seq=2 ttl=61 time=202.104ms
received from 10.0.1.149: icmp_seq=3 ttl=61 time=202.115ms
received from 10.0.1.149: icmp_seq=4 ttl=61 time=202.244ms
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max = 201.853/202.094/202.244 ms
确认之后,请将刚才设置的过滤部分取消。
# no ip filter 1
# no ip filter 2
# tunnel select 1
# no ip tunnel secure filter in
# save
![]() http://docs.aws.amazon.com/AmazonVPC/latest/GettingStartedGuide/ExerciseOverview.html
http://docs.aws.amazon.com/AmazonVPC/latest/GettingStartedGuide/ExerciseOverview.html
 QQ咨询
QQ咨询